Start Chatting Already [No Registration Required]
This will take you to the chat room you are looking for.
Shell upload attack is a vulnerability in web applications that allows an attacker to upload an executable file(php/python/perl/windows exe) through the document/image upload form. Once the file lands into your uploads directory, the attacker can run the script by navigating to example.com/uploads/c99.php
Some popular php shells are C99, r57 & p0wny
Usually, this can be simply prevented by rejecting files that have .php.pl .py .cgi .exe extension in your backend. However, just in case your uploader fails to do block a backdoor shell and its uploaded to your uploads directory, you can take the advantage of Cloudflare’s Firewall Rules and block its execution. The attacker will have no benefit if s/he’s unable to executed the uploaded file.
Login to your Cloudflare account, switch to Firewall tab, click on “Firewal Rules” tab. Now do as shown in the image below.
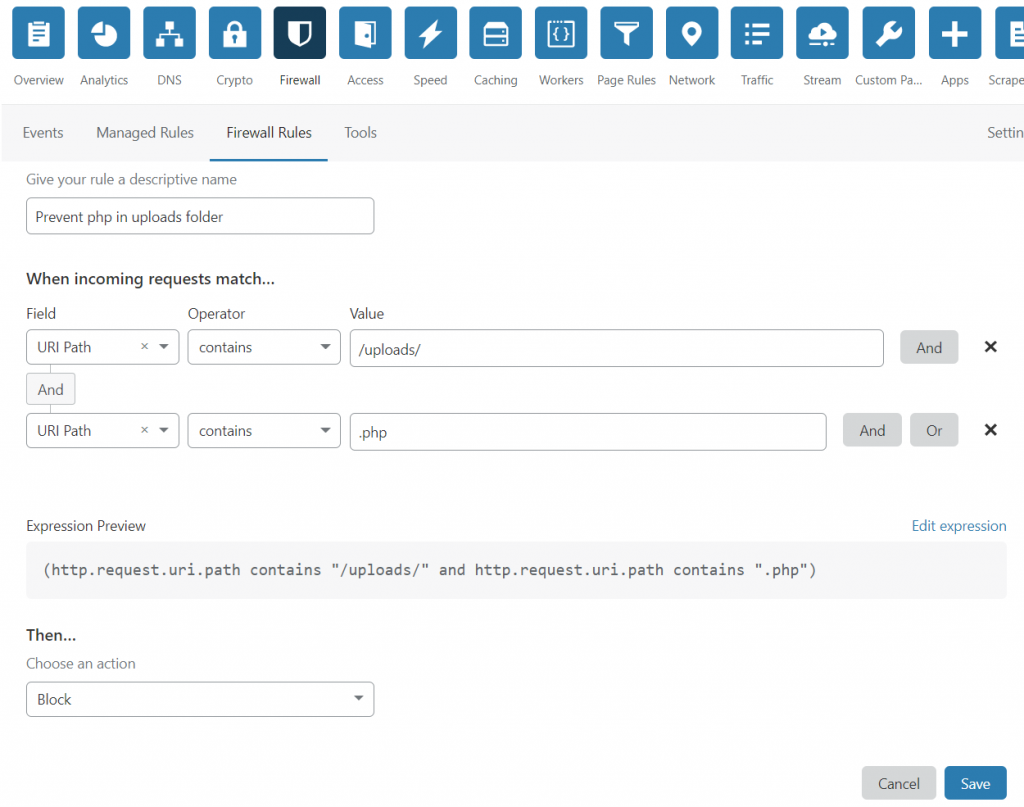
Under When incoming request match.. section, we choose “URI Path” for Field, “contains” for Operator and “/uploads/” for value. You should fill your upload directory’s name in place of /uploads/. After this we click the “And” button right before the x button. This adds one more line which we have to fill in the similar way. Once you have filled the form as shown in the image above, click the save button.
Now visit your_site.com/uploads/test.php & it will be blocked by Cloudflare.
Prevent shell from being uploaded through image uploader form with PHP
A well written uploader script can prevent malicious files from being uploaded.
Please do not do this:
//Example: A program to reject all files except jpg. How should it be done?
//Wrong approach
if(strpos($_FILES['upload']['name']), '.jpg')!==false){
die('Please only upload jpg files');
}else{
//Accept file
}
//Because a file with name image.jpg.php will easily pass. Your code should be implemented such that the last extension should be considered in case of double extension file.
//A better approach is
$extension = end(explode('.', strtolower($_FILES['upload']['name']))); //grab the part after last dot
if($extension !== 'jpg'){
die('Please only upload jpg files');
}else{
//Accept file
}Do this instead:
How to make a secure php file uploader
Because, even image.jpg or image.png file can be used to compromise your server. Wondering how?
An outdated image processing library installed on your server (GD/ ImageMagick) might have some vulnerabilities that might allow an image file to execute arbitrary code on your system. Even if you are not using those libraries, a thumbnail generator or cache plugin on your site might be using it.
The correct way is to check both the MIME type of the uploaded image & its extension to confirm its a real image.
FAQs on shell upload:
Q. Can someone hack my server with a PDF or document(doc/docx) file?
One can not hack your server with a pdf/doc/docx/xls file however, your users may be hacked with those files. From time to time, vulnerabilities are discovered in PDF readers & MS Word/ Excel.
This is because, pdf files support scripting and hence some flaw in a pdf reader can be used to download & run malware. Similar goes for MS Word/Excel which have extreme scripting capabilities.
Q. Can a image.php.jpg file containing php code be used to hack my server?
Since the last extension is .jpg, its a jpg file and it can not be used to execute php code. JPG file will be downloaded to the browser, it wont be executed on the server at all. Even in future, if one is able to find an exploit in browser or operating system’s image viewer, s/he might be able to exploit the client’s image viewer but not the server in any case (other than 0day exploits).
However, if the attacker is able to upload a .htaccess file to your uploads folder, the .htaccess file can tell your server that all jpg files should be treated as php file. For example, check the .htaccess code below
AddType application/x-httpd-php .jpgPlease submit a comment if you want me to correct something in this article.